Difference between revisions of "Samba4 Administration"
From Stadm
Jump to navigationJump to search| Line 114: | Line 114: | ||
**gpmc.msc - Group Policy Management, here you can view and edit Group Policy Objects(GPOs) applied to the domain | **gpmc.msc - Group Policy Management, here you can view and edit Group Policy Objects(GPOs) applied to the domain | ||
**eventvwr - Event Viewer, Windows log files, this is where your errors/warnings will be when troubleshooting windows | **eventvwr - Event Viewer, Windows log files, this is where your errors/warnings will be when troubleshooting windows | ||
| − | [[File:win_r_admin.png|Admin Tools]] | + | [[File:win_r_admin.png|640px|Admin Tools]] |
==MAC== | ==MAC== | ||
Revision as of 12:49, 5 December 2014
Contents
Managing Domain
- To Manage, Add Users, change settings, edit GPO's, view DNS entires, etc. for the domain it should be done from a Windows 7 or Higher, or Server 2012 or higher Computer
- Any computer on the Domain can manage the domain controller(rumba), as long as you are an Administrator to the Domain and have RSAT installed(see below)
- Because there are two domain controllers you want to make sure you are making your changes to rumba and not limbo
- NOTE: if you're going to do the following run the eadm_backup script BEFORE you make any changes to GPO, in case you mess up, these backups will save you form a nightmare
- backup script is a BASH script that stops the samba service and calls /usr/local/samba/bin/samba_backup, backups to /usr/local/backups and logs to /usr/local/backups/logs, this should be run on rumba, would not hurt you to run it on limbo just in case
/usr/local/sbin/eadm_backup
- The script will email the user defined email address(look inside the script) if anything failed, you should however go to /usr/local/backups and see that etc.{TIMESTAMP}.tar.bz2, samba_private{TIMESTAMP}.tar.bz2, and sysvol{TIMESTAMP).tar.bz2 where created and if they where not check the logs at /usr/local/backups/logs(they are also timestamped as well)
- Any GPO edits will have to be manually rsynced to limbo(you want to make your changes on rumba)
- This can and will be scripted, at the moment not enough testing has been done to ensure the script will not mess up the GPO's(basically the SYSVOL folder) which can lead to corruption and a huge headache if there are no recent backups
- How to rsync: run this command, its a dry run, ensure those are the changes and files that want to me rsynced over
- This as an IMPORTANT reminder: rsync --options SOURCE DESTINATION
- Do not mess up the SOURCE and DESTINATION addresses, this will cause corruption
- Last Note: RUN this command on LIMBO!!, you want to pull your data, not push it
rsync --dry-run -XAavz --delete-after root@rumba:/usr/local/samba/var/locks/sysvol/ /usr/local/samba/var/locks/sysvol/
- that was the dry run version, it will only tell you what files it will overwrite/write if run without the dry-run option, once you have seen the dry-run output and want to copy those files run:
rsync -XAavz --delete-after root@rumba:/usr/local/samba/var/locks/sysvol/ /usr/local/samba/var/locks/sysvol/
Install RSAT
- If not installed on your Windows Computer Remote Server Administration Tools(RSAT) will have to be downloaded and installed
- If your running a Windows Server version they are already installed you usually just must enable them(skip down to enabling RSAT after installing)
- Download Remote Server Administration Tool from the microsoft website, http://www.microsoft.com/en-us/download/details.aspx?id=7887
- Install, Once installed open up control panel and then open up programs, then programs and features
- on the left pane click "Turn Windows features on or off"
- Select all under Remote Server Administration Tool(Really just the Active Directory, Group Policy, and DNS stuff), then click okay
Creating Users
- users can be created in two ways:
- they can be done through the gui provided by RSAT(Remote Service Administration Tools) to add users into Active Directory (AD)
- simply click new user in the appropriate OU (organizational unit) and enter in name,username and password
- The AD LDAP schema has been extended to allow the storage of UIDS in Active Directory
- To change a users UID, click properties on a user under Active Directory Users and Computers, on the properties tab click UNIX Attributes
- Click the NIS Domain of EADM and give them a UID, login shell can be /bin/false or /sh(later on we'll try logging in linux users against AD)
- Give them a home(doesnt matter for now as we are not allowing linux users to authenticate against ad yet)
- Add them to a primary group, for most users the group of "Domain Users" is fine
- To create user into AD using terminal use samba-tool
samba-tool user add USERNAME
- This will create a user in the default OU of Users, to manage this user use RSAT
Giving User a Profile
- Once a user is added he might need to be given a roaming profile
- Roaming profiles live on the server, whenever a user logins in the profile is loaded from the server and the users local profile(if there is one) is update to reflect any changes that are on that roaming profile on the server, on logout the changes the user has made are sent back to the server and stored there as well as the local profile
- Key Point: On login user pulls info from server, on logout user pushes changes back, if the server is down the user can still login but he will login to the most recent local profile stored on the computer, changes will not be pushed back on logout if there is no domain controller, the system will warn you and may even log you in with a temporary profile, unless the server comes back up and you are able to logout eventually after making changes to the local profile there is a chance your roaming profile will not be updated with your settings/files
- This is a good setup for Administrators who will be logging in to multiple machines at the same time without logging out or carrying a lot of files in there profiles
- allows you to move scripts and useful files with you on login, mount a few drives and make changes, also good if your anything like me and login into 4 computers at the same time(note be careful with this) usually your profile will most accurately reflect the changes you made to the same file on the last computer you logout from(i believe timestamps are taken to consideration as well)
- Local Profiles
- Local profiles has it pros and cons
- Pros: for the default Administrator account it is perfect, no files should be carried around on an Administrator profile, all changes to the profile stay local to the machine and are not synced back to the server, if you login to two separate computers with the Administrator account all changes will stay local to there separate computers. This is probaly good as well for users who work at home but sometimes bring there laptops in to work here, at home all there files stay local to there machine they will always have what they need locally, when they connect to our network and login, GPO's can be applied and they can have network mounted drives and firewall settings implemented automatically
- Cons: For the user, there is no backup of there profile, if they have no backups and there hard drive crahes/act of god/ etc. it is gone, there would be no way to recover the users settings and files(not completely, look below at Folder Redirection)
- Folder Redirection
- Here is where it gets a little tricky, we can have folder redirection with local profiles, and we can also have folder redirection with roaming profiles, or we can have none at all
- Usually folder redirection will want to be implemented on a users Roaming Profile if in his home directory he/she has gigabytes worth of data (2-1000+GB), this will increase there login/logout times significantly as well as keep all there information on the server
- Roaming profiles with folder redirection allows the profile to be kept small(usually only the size of the AppData folder which is around 100mb), while the users profile(basically now just settings) still "Roams" the Folder setup for redirection(Usually Documents, Pictures, Videos, Music, etc.) will not roam in the same way. The Client will instead now pull and push data as changes are made, the information will reside on the local client and server, whenever the client makes a change to any Folder that is "redirected" the changes will be updated on the server immediately
- on logout only the changes that are made to the "roaming" part of the profile(again usually just APPData folder) will be pushed back to the server, the redirected folders have been synced in real time and will not have to be sent back unless a file was recently edited before logout.
- Cons: this type of setup doesn't really work if you log into a lot of machines at once. Yea your files on one machine get updated immediately if you are working on them from another, but because Folder Sync will be working on both(or more) computers at the same time trying to update al the files that change at once (including settings files that programs decide to stupidly store in Documents instead of APPData) corruption generally happens pretty quickly. If you only login to one machine and use that as your main machine you really shouldn't experience any problems, the problems arise when logging in from different machines at the same time and even different versions of windows
- Local Profiles with Folder Redirection
- Dont really have this setup anywhere but there are uses for it
- Same as above if user doesn't move between computers and wants his files on the server updated automatically, profile info(basically just settings) just live on his computer
- this is good if the user wants all his files on the server and logins in from different versions of windows(his settings will be local to each machine) this to however can be setup up with Roaming profiles
GPO Office
- admx files must be downloaded for each version of microsoft office that clients use(office 2007, 2010, etc.)
- run a "gpudate \force" if you dont see them appear in group policy editor
- once placed in policyDefinitions under sysvol GPO may be applied to that specific version of office
- User Configuration->Administrative Templates ->"Microsoft Office [version]" ->Privacy->Trust Center
- enable the "Disable opt-in..", disable "Enable Customer Experience..." and "Automatically receive small.."
- must be done for every version of office clients are running(annoying pop up messages when office starts if this is not set)
GPO Windows Update
- locate a copy of wuau.adm and install into PolicyDefinitions
- Windows update group policy should be set up on a per machine bases(GPO applied to Machines not Users)
- Computer Configuration ->Policies-> Administrative Templates ->Windows Components->Windows Update
Configure Automatic Update: Enabled Allow non-administrators to receive update notifications: enabled Allow Automatic Updates Immediate installations: enabled No auto-restart with logged in users: enabled Reschedule Automatic Updates scheduled installation: enabled
GPO Network, Firewall, Remote Desktop Connections
- GPO for RDC are in two locations
- Computer Configuration->Policies->Administrative Templates->Network->Network Connections->Windows Firewall-> Domain Profile
Windows Firewall:Allow inbound Remote Desktop conneciotns
- limit to subnets of eri and vpn
Windows Firewall: Allow ICMP exceptions: Enabled
- check Allow inbound echo Request
- Computer Configuration->Policies->Administrative Templates->Windows Components->Remote Desktop Connection Host->Connections
Allow users to connect remotely using Remote Desktop Services: enabled
- to allow specific users/group login:
- Computer Configuration->Policies->Windows Settings->Security Settings->Restricted Groups
- create Remote Desktop Users group if not created, add users manually into group or add an entire group to allow Remote Desktop Connections
- DNS suffix search list
- Computer Configuration->Policies->Administrative Templates => Netowrk => DNS client => DNS suffix search list
- Enabled: mydomain.edu, name.mydomain.edu
Profile Version for Windows Server 2012
- If you are using roaming profiles and using any of the following operating Systems you must enable the .V3 extension on roaming profiles
- Operating systems: Windows 8.1, Windows 8, Windows Server 2012 R2, or Windows Server 2012
- Link: http://technet.microsoft.com/en-us/library/jj649079.aspx
- Basically you install an update from Microsoft and edit a registry key so that Windows Server 2012 will pick up the profile with the .V3 extension instead of .V2 which is used for Windows 7
Quick Shortcuts/Tutorial
- Lets face it navigating Windows is horrible, so lets show some quick ways of getting around to important places while not wasting much time
- Search in Windows 8 is subpar(especially when looking for admin tools), however commonly used tools can be opened a lot faster if using the run prompt provided by windows
- How To Open Run Prompt: Keyboard Shortcut
- Windows Key + R
- If on a Mac and using Remote Desktop the shortcut is:
- Command + R
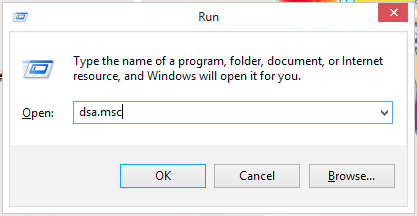
- The following prompt should pop up:
- Here is a list of important commands that can be run here that open up the applications we will use most often:
- cmd - opens up a non-administrative windows command prompt
- regedit - opens up the local computer registry editor(not needed really, registry settings can be applied via GPO)
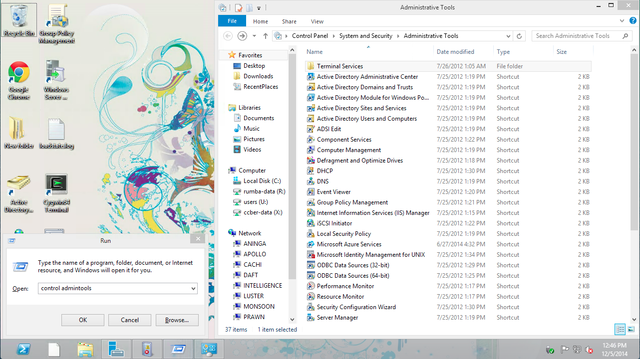
- control - opens up the Windows Control Panel where most(all) settings can be changed via GUI
- control admintools - opens up Administrative Tools, if you can't find something this is where it probably is!!!
- The rest of the list can be opened from Administrative Tools. but i included them to be accessed faster if need be:
- dsa.msc - Active Directory Users and Computers, here you can add an edit new users or computers in the domain
- gpmc.msc - Group Policy Management, here you can view and edit Group Policy Objects(GPOs) applied to the domain
- eventvwr - Event Viewer, Windows log files, this is where your errors/warnings will be when troubleshooting windows